Selamat berkunjung para visitor yang kelaparan akan informasi.
 Sekarang ane lagi bingung mau nulis apa , yang enak apa ya ... bosen juga kalau lama lama nulis tweaking dan maintenance sekali-sekali ane tulis tentang hacking tapi yang mudah mudah aja.
Sekarang ane lagi bingung mau nulis apa , yang enak apa ya ... bosen juga kalau lama lama nulis tweaking dan maintenance sekali-sekali ane tulis tentang hacking tapi yang mudah mudah aja.
langsung saja sekarang kita membahas tentang DDOS.
apa itu DDOS ? simak aja artikel ini :
DDoS attack adalah Distributed-Denial-of-Service attack, sebuah usaha untuk membuat suatu sumber daya komputer menjadi tidak bisa dipakai oleh user-nya, dengan menggunakan ribuan zombie system yang ‘menyerang’ secara bersamaan. Tujuannya negatif, yakni agar sebuah website atau layanan online tidak bisa bekerja dengan efisien atau bahkan mati sama sekali, untuk sementara waktu atau selama-lamanya. DDoS attack adalah salah satu model dari DoS ( denial-of-service) attack.
Target serangan DoS attack bisa ditujukan ke berbagai bagian jaringan. Bisa ke routing devices, web, electronic mail, atau server Domain Name System.
Ada 5 tipe dasar DoS attack :
1. Penggunaan berlebihan sumber daya komputer, seperti bandwith, disk space, atau processor.
2. Gangguan terhadap informasi konfigurasi, seperti informasi routing.
3. Gangguan terhadap informasi status, misalnya memaksa me-reset TCP session.
4. Gangguan terhadap komponen-komponen fisik network.
5. Menghalang-halangi media komunikasi antara komputer dengan user sehingga mengganggu komunikasi.
DoS attack juga termasuk eksekusi malware, yang dimaksudkan untuk :
* Memaksimalkan kerja processor, sehingga memblok tugas-tugas yang lain.
* Memicu terjadinya error di dalam microcode.
* Memicu error pada urutan instruksi dan memaksa komputer menjadi tidak stabil dan locked-up.
* Memanfaatkan error-error yang ada di system operasi yang berbuntut pada ‘kematian’ system.
* Membuat system operasi menjadi crash.
* iFrame (D)DoS, di dalamnya terdapat sebuah dokumen HTML yang sengaja dibuat untuk mengunjungi halaman web ber-kilobyte tinggi dengan berulang-ulang, hingga melampaui batas bandwith.
Gejala-gejala DDoS attack :
* Kinerja jaringan menurun. Tidak seperti biasanya, membuka file atau mengakses situs menjadi lebih lambat.
* Fitur-fitur tertentu pada sebuah website hilang.
* Website sama sekali tidak bisa diakses.
* Peningkatan jumlah email spam yang diterima sangat dramatis. Tipe DoS yang ini sering diistilahkan dengan “Mail Bomb”.
Contoh kasus DoS attack :
1. Februari 2007, lebih dari 10.000 server game online seperti Return to Castle Wolfenstein, Halo, Counter-Strike, diserang oleh group hacker “RUS”. DDoS attack berasal dari 1.000 lebih komputer yang terletak di negara bekas Uni Sovyet. Kebanyakan berasal dari Rusia, Uzbekistan dan Belarusia.
2. Juli 2008, banyak blog milik blogger-blogger konservatif, termasuk Macsmind.com, merasa mendapat serangan DDoS attack hingga beberapa terpaksa harus offline. Serangan ini dikaitkan dengan 3 IP address yang diregister melalui GoDaddy.com ke barrackobama.com, situs resmi calon presiden AS dari partai Demokrat, Barrack Obama. Sebelumnya, beberapa pendukung Obama juga melakukan serangan ke situs-situs pendukung Hillary Rodham Clinton dengan menggunakan google.com. Sampai 8 Agustus kemarin, asal pasti serangan masih belum jelas, namun Obama atau tim kampanyenya secara personal dianggap terlibat.
Sudah faham ? ,
kalau begitu kita langsung praktek aja deh cape ngomong terus ...
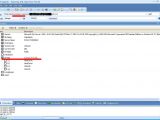
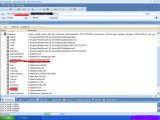
Tutorial : Pertama tama kalian semua harus memiliki koneksi internet tidak perlu harus mempunya bandwith besar terus kalian download softwarenya disini beberapa antivirus seperti avast, avg atau NOD32 akan mendeteksi file tersebut adalah virus sebaiknya disablekan dulu antivirusnya apa bila ingin menggunakannya (sebaiknya jangan) setelah di download buka file tersebut nanti akan timbul gambar seperti ini masukkan alamat ip korban pada kolom yang tertulis "localhost" apabila anda tidak mengetahui ip addresnya klik menu "toolz" pilih "URL To IP Converter" tinggal tekan "Attack"
NB:Untuk Server Yang Kuat Gunakan Beberapa Komputer sekaligus serta ubah "interval" nya menjadi lebih kecil.
cocok buat ngerjain temen atau server sekolah yang lagi Deadline entry nilai ane juga pernah pake cara ini pas kelas 1 sma biar bisa remedial gitu, bagi yang belom ngerti bisa di baca lagi kok dan ane mau nambahin nih software DDOS itu segudang macam nya semakin banyak komputer yang melakukan DDOS semakin lemot tuh server ...
ok sampai disini perjumpaan kite wassalam .
 Sekarang ane lagi bingung mau nulis apa , yang enak apa ya ... bosen juga kalau lama lama nulis tweaking dan maintenance sekali-sekali ane tulis tentang hacking tapi yang mudah mudah aja.
Sekarang ane lagi bingung mau nulis apa , yang enak apa ya ... bosen juga kalau lama lama nulis tweaking dan maintenance sekali-sekali ane tulis tentang hacking tapi yang mudah mudah aja.langsung saja sekarang kita membahas tentang DDOS.
apa itu DDOS ? simak aja artikel ini :
DDoS attack adalah Distributed-Denial-of-Service attack, sebuah usaha untuk membuat suatu sumber daya komputer menjadi tidak bisa dipakai oleh user-nya, dengan menggunakan ribuan zombie system yang ‘menyerang’ secara bersamaan. Tujuannya negatif, yakni agar sebuah website atau layanan online tidak bisa bekerja dengan efisien atau bahkan mati sama sekali, untuk sementara waktu atau selama-lamanya. DDoS attack adalah salah satu model dari DoS ( denial-of-service) attack.
Target serangan DoS attack bisa ditujukan ke berbagai bagian jaringan. Bisa ke routing devices, web, electronic mail, atau server Domain Name System.
Ada 5 tipe dasar DoS attack :
1. Penggunaan berlebihan sumber daya komputer, seperti bandwith, disk space, atau processor.
2. Gangguan terhadap informasi konfigurasi, seperti informasi routing.
3. Gangguan terhadap informasi status, misalnya memaksa me-reset TCP session.
4. Gangguan terhadap komponen-komponen fisik network.
5. Menghalang-halangi media komunikasi antara komputer dengan user sehingga mengganggu komunikasi.
DoS attack juga termasuk eksekusi malware, yang dimaksudkan untuk :
* Memaksimalkan kerja processor, sehingga memblok tugas-tugas yang lain.
* Memicu terjadinya error di dalam microcode.
* Memicu error pada urutan instruksi dan memaksa komputer menjadi tidak stabil dan locked-up.
* Memanfaatkan error-error yang ada di system operasi yang berbuntut pada ‘kematian’ system.
* Membuat system operasi menjadi crash.
* iFrame (D)DoS, di dalamnya terdapat sebuah dokumen HTML yang sengaja dibuat untuk mengunjungi halaman web ber-kilobyte tinggi dengan berulang-ulang, hingga melampaui batas bandwith.
Gejala-gejala DDoS attack :
* Kinerja jaringan menurun. Tidak seperti biasanya, membuka file atau mengakses situs menjadi lebih lambat.
* Fitur-fitur tertentu pada sebuah website hilang.
* Website sama sekali tidak bisa diakses.
* Peningkatan jumlah email spam yang diterima sangat dramatis. Tipe DoS yang ini sering diistilahkan dengan “Mail Bomb”.
Contoh kasus DoS attack :
1. Februari 2007, lebih dari 10.000 server game online seperti Return to Castle Wolfenstein, Halo, Counter-Strike, diserang oleh group hacker “RUS”. DDoS attack berasal dari 1.000 lebih komputer yang terletak di negara bekas Uni Sovyet. Kebanyakan berasal dari Rusia, Uzbekistan dan Belarusia.
2. Juli 2008, banyak blog milik blogger-blogger konservatif, termasuk Macsmind.com, merasa mendapat serangan DDoS attack hingga beberapa terpaksa harus offline. Serangan ini dikaitkan dengan 3 IP address yang diregister melalui GoDaddy.com ke barrackobama.com, situs resmi calon presiden AS dari partai Demokrat, Barrack Obama. Sebelumnya, beberapa pendukung Obama juga melakukan serangan ke situs-situs pendukung Hillary Rodham Clinton dengan menggunakan google.com. Sampai 8 Agustus kemarin, asal pasti serangan masih belum jelas, namun Obama atau tim kampanyenya secara personal dianggap terlibat.
Sudah faham ? ,
kalau begitu kita langsung praktek aja deh cape ngomong terus ...
Tutorial : Pertama tama kalian semua harus memiliki koneksi internet tidak perlu harus mempunya bandwith besar terus kalian download softwarenya disini
Code:
http://www.kitaupload.com/download.php?file=585dos%20web..zip
NB:Untuk Server Yang Kuat Gunakan Beberapa Komputer sekaligus serta ubah "interval" nya menjadi lebih kecil.
cocok buat ngerjain temen atau server sekolah yang lagi Deadline entry nilai ane juga pernah pake cara ini pas kelas 1 sma biar bisa remedial gitu, bagi yang belom ngerti bisa di baca lagi kok dan ane mau nambahin nih software DDOS itu segudang macam nya semakin banyak komputer yang melakukan DDOS semakin lemot tuh server ...
ok sampai disini perjumpaan kite wassalam .
Tags: