User passwords and product serial numbers potentially exposed

A self-proclaimed grey-hat hacker has located a critical SQL injection vulnerability in a website belonging to security giant Symantec. The flaw can be leveraged to extract a wealth of inf
ormation from the database including customer and admin login credentials, product serial numbers, and possibly credit card information.
The flaw was found by a Romanian hacker going by the online handle of Unu, according to whom an insecure parameter of a script from the pcd.symantec.com website, allows for a blind SQL injection (SQLi) attack to be performed. In such an attack, the hacker obtains read and/or write permission to the underlying database of the vulnerable website.
During a regular SQLi attack, the result of a rogue SQL query is displayed inside the browser instead of the normal web page output. Meanwhile, in a blind SQL injection, the query executes, but the website continues to display normally, making it much more difficult to extract information.
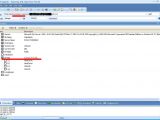 |
From the screen shots released by Unu there are many potentially interesting databases, but the one he chose to look at is called "symantecstore." One of the tables in this database is named "PaymentInformationInfo" and contains columns such as BillingAddress, CardExpirationMonth, CardExpirationYear, CardNumber, CardType, CcIssueCode, CustomerEmail, CustomerFirstName, CustomerLastName or SecurityIndicator.
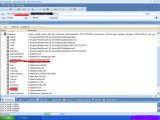 |
For demonstration purposes, he extracted 6 of these entries at random, revealing customer names and login credentials with the passwords stored in plain text; a major security oversight. The hacker also notes that passwords for the accounts in a different table called TB_EMPLOYEE are also stored in a similar insecure way.
A third table Unu chose to investigate is called TB_ORDER and contains columns such as ProductName, ProductNumber, SaleAmount and SerialNumber. There are 122,152 entries in the SerialNumber column.
This is not the first time when Unu scrutinizes the security of websites belonging to antivirus vendors. His previous targets includes Kaspersky and Bitdefender. Some months back, he even disclosed a vulnerability affecting a different Symantec website. The AV company eventually played down its impact.
At the end of his most recent disclosure, Unu mentions his previous attack against Kaspersky's US online store website. "There was fair play, they quickly secured vulnerable parameter, and even if at first they were very angry at me, finally understood that I did not extract, I saved nothing, I did not abused in any way by those data found. My goal was, what is still, to warn. To call attention [sic.]," the hacker writes on his blog.
Note: We have alerted Symantec about the potential security breach. We will update this article when/if more information becomes available.
Update: In an e-mail to Softpedia, Symantec has confirmed the existence of a vulnerabiliy in the pcd.symantec.com. Here is the full statement we received:
"A SQL injection vulnerability has been identified at pcd.symantec.com. The Web site facilitates customer support for users of Symantec's Norton-branded products in Japan and South Korea only. This incident does not affect Symantec customers anywhere else in the world.
"This incident impacts customer support in Japan and South Korea but does not affect the safety and usage of Symantec's Norton-branded consumer products. Symantec is currently in the process of updating the Web site with appropriate security measures and will bring it back online as soon as possible. Symantec is still investigating the incident has no further details to share at this time."


















0 comments:
Post a Comment